


Severity of code execution bug mitigated by ‘high uptake’ of previous patch. Zyxel has released patches for several of its firewall products following the discovery of...



Open source analytics platform fixes bug that could lead to authentication bypass, privilege escalation. Malicious actors could take over an administrator account in Grafana due to...
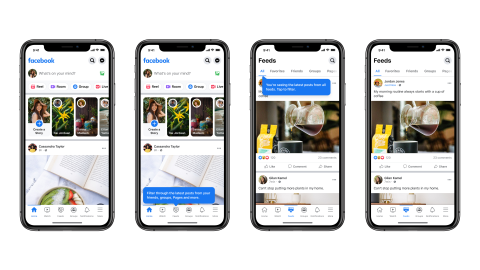
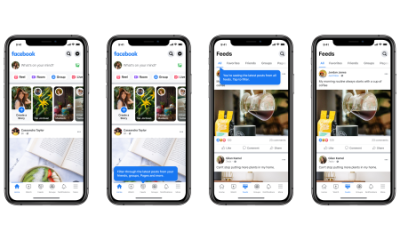

Facebook has unveiled a new look for its mobile app, as it moves towards becoming more of a ‘discovery engine’ than just a social network. The...



Unauthenticated SQL injection bugs put thousands of WordPress sites under threat. A researcher at security firm Cyllective has unearthed vulnerabilities in dozens of WordPress plugins, affecting...



Broader architectural failings of Chinese vendor potentially puts 1.5m devices at risk. A raft of zero-day flaws found in a popular automotive GPS tracking device “could have disastrous...



DID has been designed to give users and organizations greater security and privacy. Decentralized Identifiers (DID) is now an official web standard, according to a news release from...



Are you part of those searching for Kuda Bank loan?, Kuda Bank loan interest rate? Or How to borrow money from Kuda Bank?. Answers to most...



Creating an email list is an essential part of email marketing. There are different ways marketers can gather emails using creative approaches. But sometimes, there is...



As far back as the English Civil War in 1643, soldiers have credited objects in their pockets — usually bibles — with blocking bullets that could...



New update addresses challenges faced by users in repressive countries. A new release of Tor Browser enables users to circumvent location-specific censorship to connect to the...

An unauthenticated arbitrary object instantiation vulnerability in LDAP Account Manager (LAM) has been discovered during an internal penetration test. LAM is a PHP web application for...



Inaugural report from cyber safety panel outlines strengths and weaknesses exposed by momentous security flaw. The ‘Log4Shell’ vulnerability in open source library Log4j has reached “endemic” proportions and...



Chain of exploits could be triggered without any authentication. Blitz.js, a JavaScript web application framework, has patched a dangerous prototype pollution vulnerability that could lead to remote code...



In the wake of the Ethereum crash, it’s important to keep your head clear. You should pay attention to market capitalization and invest in new assets...



New research shows how electromagnetic interference can be used to trigger arbitrary behavior on mobile touchscreens, although caveats apply. Some attacks on smartphones require physical access...



#FeatureByitel: Enjoy Great Products With itel, The Smart Life Brand. Better life is here and the brand championing this message is none other than itel. The brand...



New hacking technique allows threat actors to evade some of the most effective phishing countermeasures. A new way of carrying out phishing attacks is being adopted...



Privacy concerns raised over mandate to retain customer records. ANALYSIS Virtual private network (VPN) providers are digging in their heels, following the introduction of a new law...



Authentication controls added to defend against account hijack threat. The English Premier League has introduced two-factor authentication (2FA) controls to its official Fantasy Premier League game (FPL), offering...



Mozilla’s message to MEPs appears to be gaining traction, says senior public policy manager at the non-profit. Mozilla has stepped up its efforts to dissuade EU...