Technology
BHUSA: Make sure your security bug bounty program doesn’t lead to a data leak of its own.
Researchers, organizations, and bug disclosure platforms can all make improvements to help protect user data
Bug bounty programs can be a useful part of a layered security approach, but stakeholders have been urged to maintain a tight grip on their data handling practices throughout the disclosure process to avoid creating a data leak of their own.
At Black Hat USA yesterday (August 11), delegates were told how research oversights and shoddy data governance principles across the bug bounty market have resulted in the leak of users’ personally identifiable information. And what’s more, this data is often still available long after the corresponding ticket has been closed.
In an interesting presentation, Dylan Ayrey, CEO of Truffle Security (the company behind TruffleHog), and Whitney Merrill, data protection officer and lead privacy counsel at software firm Asana, took a closer look at the potential pitfalls of the bug bounty disclosure process – starting with researchers.
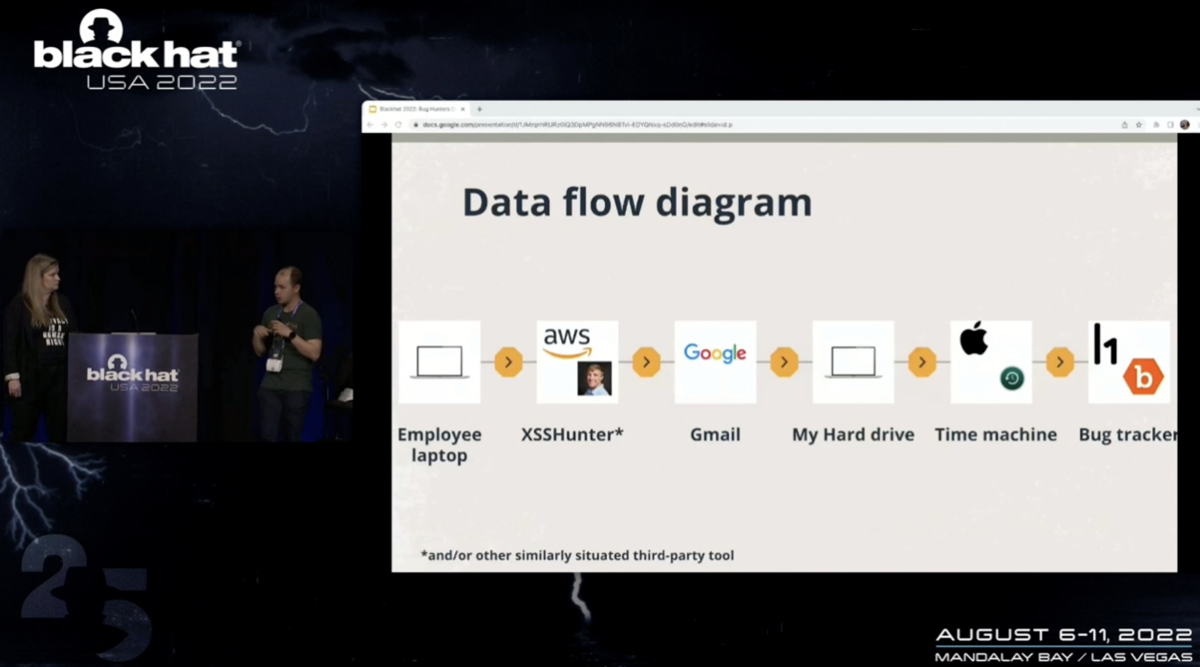
Data gleaned from bug bounties can end up being stored in a wide range of systems
Citing real-world examples, Ayrey said that while many bug bounty programs prohibit researchers from accessing user data, this does still happen. For instance, a blind cross-site scripting (XSS) exploit could trigger on an administrator endpoint, resulting in the dump of the entire user database.

Data gleaned from bug bounties can end up being stored in a wide range of systems
This user data could then be pushed to various third-party storage systems, along with being appended to the bug bounty program’s issue tracker – all of which then become a potential leak vector of their own.
Scaled up across the many hundreds of programs out there, this could result in a wealth of potentially sensitive data being stored in various places for an extended period.
Leave no trace
In addition to accidental research discoveries, Ayrey and Merrill said that organizations and bug bounty platforms are also opening the door to leaks through their failure to request that bug hunters delete all relevant data, or by simply leaving the sensitive information on file, long after the bug support ticket has been closed.
Offering advice to those who host bug bounty programs, Merrill said: “We’re probably not going to get to ‘perfect’, but we can take incremental steps to move forward. Basic data governance principles and data lifecycle best practises will help get you there.”
Ayrey added: “These privacy leaks in bug bounties are really common, and for every example that we can share publicly there are 100 examples that can’t be shared publicly. I think it’s time that we start a conversation about it and reduce some of the impact of this.
“We do believe that bug bounties are a positive force for change, and that companies that run bug bounties are in a better place than companies that don’t.”

-

 Technology2 years ago
Technology2 years agoVoIP Number: Everything You Need To Know
-

 Music1 month ago
Music1 month ago[Music] Gnash Ft Olivia O’Brien – I Hate you, I Love you
-

 Music1 month ago
Music1 month ago[INSTRUMENTAL] John Legend – All Of Me
-

 Music1 month ago
Music1 month agoAlan Walker – Faded [INSTRUMENTAL]
-

 Music1 month ago
Music1 month ago[Video] 21 Savage ft. Offset & Metro Boomin – Rap Saved Me
-

 Music1 month ago
Music1 month ago[Instrumental] Wiz Khalifa – See You Again ft. Charlie Puth
-

 ANE Stories4 months ago
ANE Stories4 months ago[STORY] AMAKA THE LESBIAN (Complete Episodes)
-

 Music1 month ago
Music1 month ago[Music] Akon – Sorry Blame It On Me