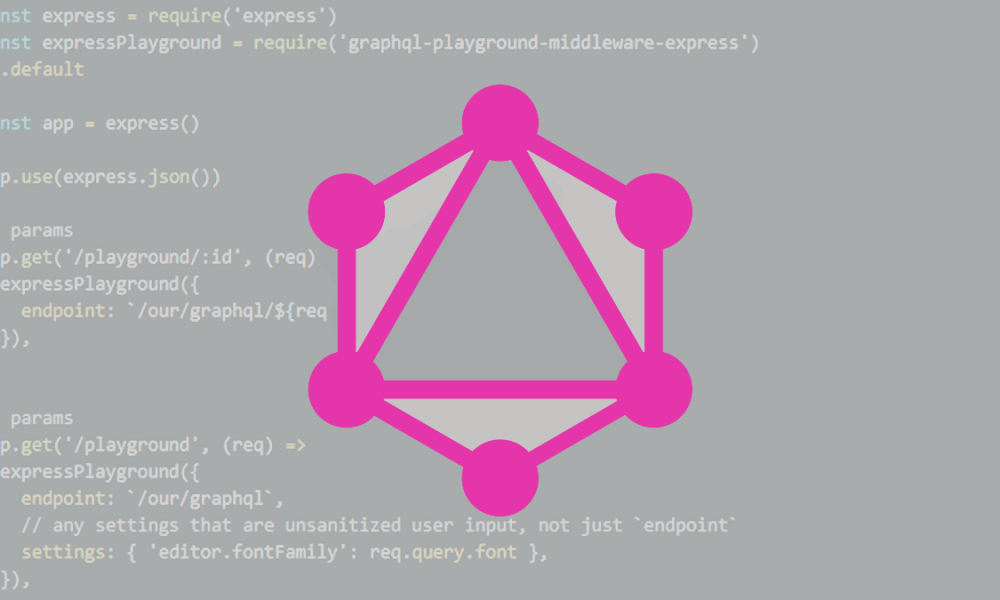

Norwegian software firm Ibexa is urging users to apply a new patch immediately to resolve a sensitive data leak vulnerability impacting its Digital Experience Platform (DXP)....



The team behind the Cobalt Strike penetration testing tool has responded to reports of a failed remote code execution (RCE) exploit patch with a new fix. HelpSystems’ Cobalt...



Windows servers running Microsoft Office Online Server can be exploited to achieve server-side request forgery (SSRF) and thereafter remote code execution (RCE) on the host, according to security...


Two Italian security researchers have netted more than $46,000 in bounties for the discovery of an Akamai misconfiguration, despite receiving nothing from Akamai itself. Akamai is...


A recently resolved vulnerability in Sophos Firewall has been abused by attackers in targeted attacks, the vendor warns. The critical vulnerability (CVE-2022-3236) poses a remote code execution (RCE) risk. Sophos...



Issue present in pingback requests feature. Researchers have gone public with a six-year-old blind server-side request forgery (SSRF) vulnerability in a WordPress Core feature that could enable distributed...



A critical command injection vulnerability in a Bitbucket product could allow an attacker to execute arbitrary code, researchers warn. Bitbucket is a Git-based source code repository hosting service...



Eco-friendly upgrade sends bounties soaring as computational demands plummet. Bug bounty rewards for the Ethereum blockchain have quadrupled for a two-week period when related to the...

Spring4Shell and Veeam RCE exploit topped the list in Q1 2022 API-related security vulnerabilities continue to be a thorn in the side of organizations, with access...



Flaws discovered in various PostgreSQL-as-a-Service offerings, including those from Microsoft and Google. Wiz Research has found vulnerabilities in popular ‘PostgreSQL-as-a-Service’ offerings from various cloud vendors, introduced...



Open source analytics platform fixes bug that could lead to authentication bypass, privilege escalation. Malicious actors could take over an administrator account in Grafana due to...



The friendly image sent by your colleague on a teleconference may be hiding a malicious secret. A security researcher has found that attackers could abuse the...



Flaw in Amazon’s Kubernetes service has since been fixed. A vulnerability in AWS IAM Authenticator for Kubernetes could allow a malicious actor to impersonate other users...