Technology
Lockdown Mode: Apple offers $2m bug bounty for vulnerabilities in new anti-spyware tech
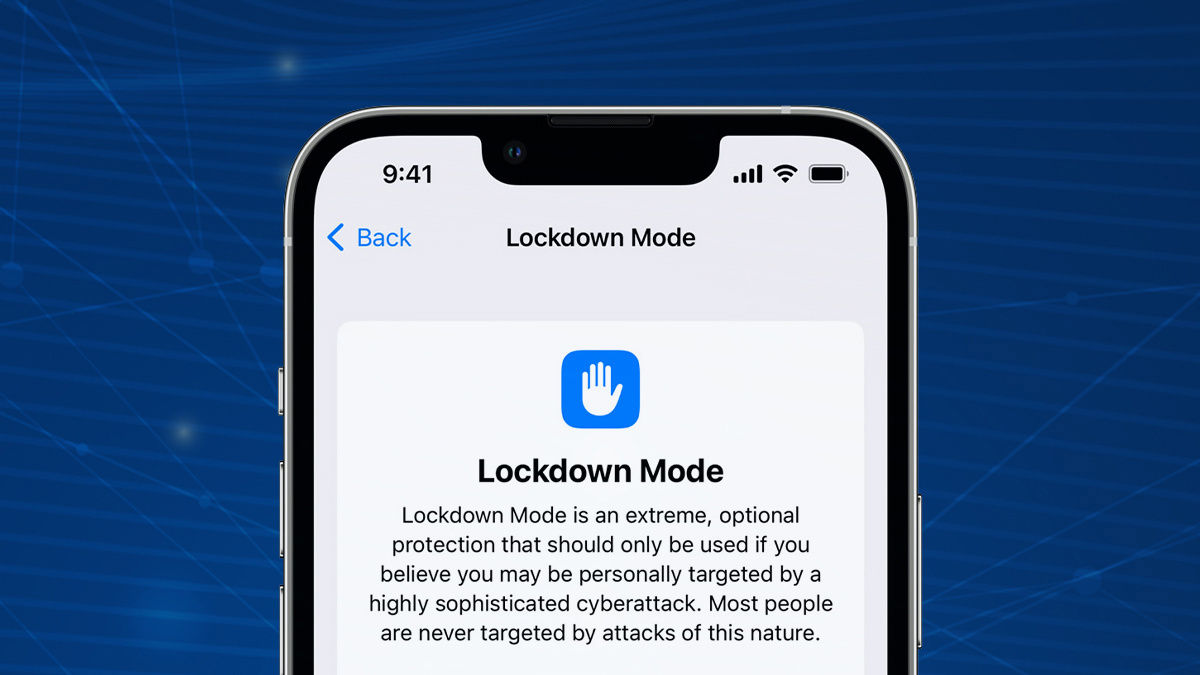
Apple has launched a security bug bounty for its new Lockdown Mode feature, which aims to give users heightened protection against spyware attacks.
Lockdown Mode, which will ship with iOS 16, iPadOS 16, and macOS Ventura, is “an extreme, optional protection for the very small number of users who face grave, targeted threats to their digital security”.
The feature is designed to thwart against targeted attacks from the growing number of private companies developing mercenary spyware for nation-states around the world.
Announcing the news last night (July 6), Apple said it will be available to users this fall.
Bug bounty offerings
Apple also revealed it has established a new category within the Apple Security Bounty program to reward researchers who find Lockdown Mode bypasses and help improve its protections.
Bounties are doubled for qualifying findings in Lockdown Mode, up to a maximum of $2 million — one of the highest maximum bug bounty payouts in the industry.
Some of the optional protections on offer through Lockdown Mode include blocking attachments other than images and disabling link previews in messages.
It’s also possible to disable web technologies such as just-in-time (JIT) JavaScript compilation for untrusted websites, along with blocking communication requests, including FaceTime calls, if the user has not previously sent the initiator a call or request.
Wired connections with a computer or accessory are also blocked when iPhone is locked, configuration profiles cannot be installed, and the device cannot enroll into mobile device management (MDM) while Lockdown Mode is turned on.
“Lockdown Mode is a groundbreaking capability that reflects our unwavering commitment to protecting users from even the rarest, most sophisticated attacks,” said Ivan Krstić, Apple’s head of security engineering and architecture.
“While the vast majority of users will never be the victims of highly targeted cyber-attacks, we will work tirelessly to protect the small number of users who are. That includes continuing to design defenses specifically for these users, as well as supporting researchers and organizations around the world doing critically important work in exposing mercenary companies that create these digital attacks.”

-

 Technology2 years ago
Technology2 years agoVoIP Number: Everything You Need To Know
-

 Music1 month ago
Music1 month ago[Music] Gnash Ft Olivia O’Brien – I Hate you, I Love you
-

 Music1 month ago
Music1 month ago[INSTRUMENTAL] John Legend – All Of Me
-

 Music2 months ago
Music2 months agoAlan Walker – Faded [INSTRUMENTAL]
-

 Music1 month ago
Music1 month ago[Video] 21 Savage ft. Offset & Metro Boomin – Rap Saved Me
-

 Music1 month ago
Music1 month ago[Instrumental] Wiz Khalifa – See You Again ft. Charlie Puth
-

 ANE Stories4 months ago
ANE Stories4 months ago[STORY] AMAKA THE LESBIAN (Complete Episodes)
-

 Music2 months ago
Music2 months ago[Music] Akon – Sorry Blame It On Me















































