Technology
Prototype pollution in Blitz.js leads to remote code execution

Chain of exploits could be triggered without any authentication.
Blitz.js, a JavaScript web application framework, has patched a dangerous prototype pollution vulnerability that could lead to remote code execution (RCE) on Node.js servers.
Prototype pollution is a type of JavaScript vulnerability that allows attackers to exploit the rules of the programming language to change an application’s behavior and compromise it in various ways.
The new bug, discovered and reported by researchers at Sonar, allowed attackers to manipulate the code in the Blitz.js app to create a reverse shell and run arbitrary commands on the server.
Prototype vulnerability in dependencies
“Blitz.js is an upcoming JS framework that gained traction on GitHub,” Paul Gerste, vulnerability researcher at Sonar, told The Daily Swig. “We selected it in order to help secure its code base and study real-world vulnerabilities.”
Blitz is built on top of Next.js, a React-based framework, and adds components to turn it into a full-stack web development platform.
One of the advertised features of Blitz.js is its ‘Zero-API’ layer, which allows the client to invoke server-side business logic through simple functions without the need to write API code.
Blitz.js makes an RPC call to the server in the background and returns the response to the client function call.
“Blitz.js adds an RPC layer on top of Next.js (among other features), and that layer uses superjson to deserialize data from incoming requests. The vulnerability is entirely inside of superjson,” Gerste said.
As an extended version of JSON, superjson adds support for dates, regexes, and circular dependencies. The circular dependency feature allows JSON specifications to reference property names, which caused the prototype vulnerability. An attacker could use these property names to change the running code on the server.
RCE on Blitz servers
Gerste discovered a chain of exploits that could be triggered through the prototype pollution vulnerability and lead to RCE.
First, a polluted JSON request is sent to the server, which triggers the routing mechanism of Blitz.js to load a JavaScript file with the polluted prototype. This allows the attacker to use the malicious JavaScript object to execute arbitrary code.
Ideally, an attacker would create and run a file on the server. But Blitz.js does not support upload functionality. However, it has a CLI wrapper script that uses JavaScript’s spawn() function to launch a new process.
The attacker could use this function to launch a CLI process and run an arbitrary command on the server.
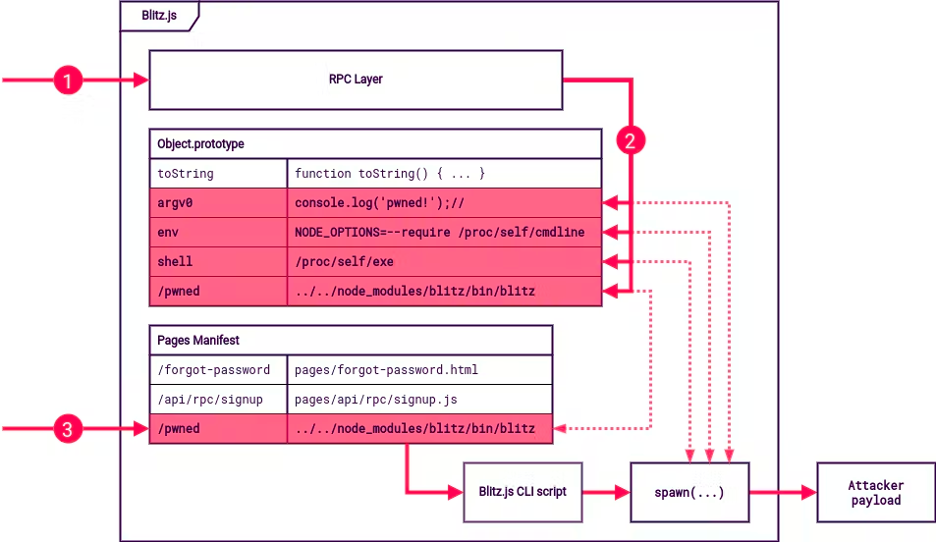
Prototype pollution in Blitz.js
What makes this vulnerability especially dangerous is that it can be triggered without any authentication, which means any user who can access the Blitz.js application will be able to launch RCE attacks.
“An attacker would have the same level of privilege as the vulnerable application,” Gerste said. “So, if the application runs as root, the attacker would also have root privileges.”
Complicated bug
Prototype pollution bugs often act in very complicated ways. For example, in the case of Blitz.js, the CLI wrapper object was not vulnerable per se but could be abused by the prototype pollution bug.
“This attack technique leverages a code pattern that isn’t a vulnerability in itself,” Gerste said. “Prototype pollution can influence the target application in a very invasive way, and it would require a lot of work to get rid of all code that could be influenced by prototype pollution.”
In his write-up of the bug, Gerste gives some general recommendations that can harden JavaScript apps against prototype pollution, including freezing Object.prototype or using the –disable-proto=delete flag in Node.js.
“I think prototype pollution is still unknown to many JavaScript developers,” Gerste said. “I don’t see developers use the patterns that we recommended in our article very often. With our blog posts, we try to help educate JavaScript developers and share this knowledge.”

-

 Technology2 years ago
Technology2 years agoVoIP Number: Everything You Need To Know
-

 Music3 weeks ago
Music3 weeks ago[Music] Gnash Ft Olivia O’Brien – I Hate you, I Love you
-

 Music2 weeks ago
Music2 weeks ago[INSTRUMENTAL] John Legend – All Of Me
-

 Music3 weeks ago
Music3 weeks agoAlan Walker – Faded [INSTRUMENTAL]
-

 Music2 weeks ago
Music2 weeks ago[Video] 21 Savage ft. Offset & Metro Boomin – Rap Saved Me
-

 Music3 weeks ago
Music3 weeks ago[Instrumental] Wiz Khalifa – See You Again ft. Charlie Puth
-

 ANE Stories3 months ago
ANE Stories3 months ago[STORY] AMAKA THE LESBIAN (Complete Episodes)
-

 Music3 weeks ago
Music3 weeks ago[Music] Akon – Sorry Blame It On Me